Last week, four SonarSourcers traveled to London to attend our third Black Hat event of the year.
Black Hat Europe was an excellent opportunity to share our Clean Code vision and its benefits for software security, a sentiment shared by most attendees who came to our booth. This reinforces our trust in the Clean Code approach and that it's not just a best practice—it's the foundation of secure software development.
Generative AI was also understandably on everyone's lips. They are indubitably great tools for developers' velocity; yet, as for human-created code, it does not come with any guarantee. This code also needs to be analyzed and reviewed, which is not a trivial task for humans as the volume of AI-generated code keeps on growing.

And because it came as a surprise for many people at our booth, we'll also repeat it in this blog post: you can get all these benefits for free!
- SonarQube for IDE, our code editor companion for Eclipse, VS Code, Visual Studio, and the majority of the JetBrains suite, can be installed directly from the respective marketplaces. You don't need to be a SonarQube Server or SonarQube Cloud user to have it!
- SonarQube Server, our best-in-class and on-premise Clean Code solution, has a free Community Build;
- SonarQube Cloud, our Clean-Code-as-a-Service technology, is free for publicly accessible projects, i.e. open-source.
Proactive Application Security: It's All About Clean Code!

Our very own Andrew Osborne and Thomas Chauchefoin also gave a 20-minute presentation on the benefits of the Clean Code approach for proactive security. It may seem a bit adventurous to present this at a security-only event such as Black Hat—and that's the point!
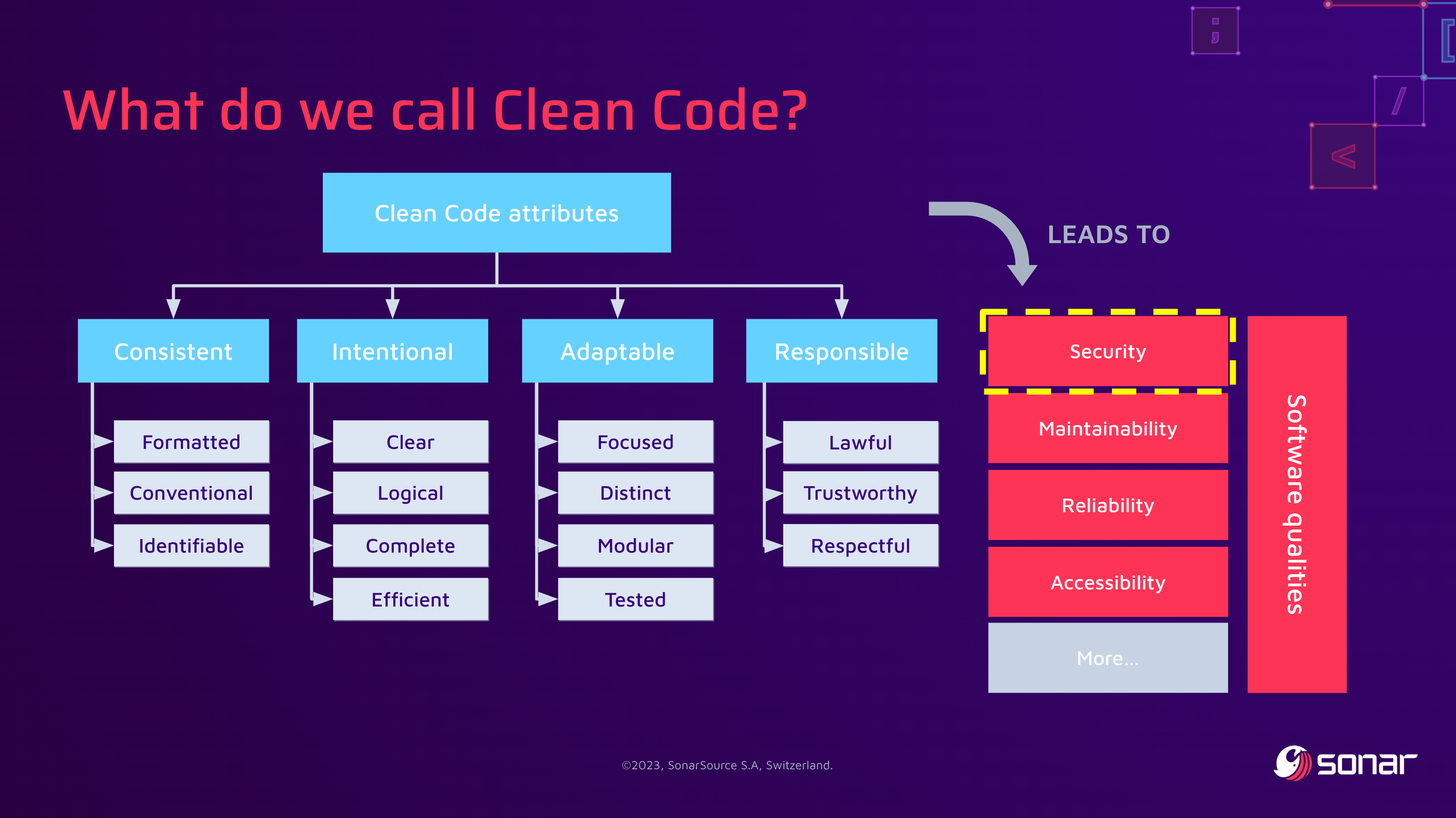
First, we had to develop why we think quality and security are indissociable. Without most Clean Code attributes, the software will lack essential properties that make it Secure. For instance, if code is neither consistent nor intentional, it will be much harder for other developers to dive into the code base and be confident in their changes.
But most of the time, vulnerabilities are unplanned emergencies: they need to be mitigated fast, and these changes should not break the affected component! Unclear and "spaghetti" code will make this task much more difficult. We also re-assessed that even apparently harmless quality defects can break the software's security properties, so addressing them will help build a good security posture.
Over the years, we've also seen an increasing interest in Shift Left practices from many security companies, but we feel like something is missing. Security tools should not be shifted as-is to developers, as they often poorly integrate with their development workflow and introduce non-negligible friction: too much switching from the code editor, many false positives, the wrong level of education, etc.
In 2023, an obvious answer to this problem would be to rely on off-the-shelf LLMs already integrated into code editors, such as GitHub Copilot, to detect unclean code. As Thomas developed in the presentation, we believe there's still considerable value in more "conventional" SAST techniques. First, he shared the details of CVE-2021-29447 (WordPress 5.7 XXE Vulnerability), a good example that security is sometimes a matter of niche knowledge that's outside the training dataset of these models.
Then, he got into the specifics of a critical vulnerability discovered by the Sonar R&D team in the NETGEAR RAX30 router (Patches, Collisions, and Root Shells: A Pwn2Own Adventure), caused by the use of an unsafe C function family. Here, it's again trivial to detect, and its exploitation doesn't only require "intelligence" but also more human traits like creativity and curiosity.
Thanks to tools catching such issues early in development, security teams can spend less time checking and focusing on security design. There will always be security issues in code, and that's fine, but security teams can help reduce their exploitability with environmental changes that can sometimes eradicate entire bug classes. They can also help craft more precise SAST tooling based on domain-specific knowledge and previous findings from internal and external audits.
And… that's a wrap for this year! Our SonarSourcers traveled the world and delivered more than 100 presentations in 2023 alone, and we are looking forward to 2024 to show you always more security research and insights on Clean Code.

