We are happy to announce our sixth consecutive Code Security Advent Calendar! Born at RIPS in 2016, each calendar comprises 24 little code puzzles containing hidden security vulnerabilities that wait to be spotted. This is our way to share good vibes with the community while learning and having fun together!
How you can participate
Starting on December 1st, we will release our code challenges on Twitter on a daily basis. Can you spot the vulnerabilities?
Follow us on Twitter to be notified of each challenge, share it with your friends, and discuss solutions and feedback in the comments. We will join the discussion and share our intended solutions.
Challenge accepted? Follow @SonarSource on Twitter.
What you can expect
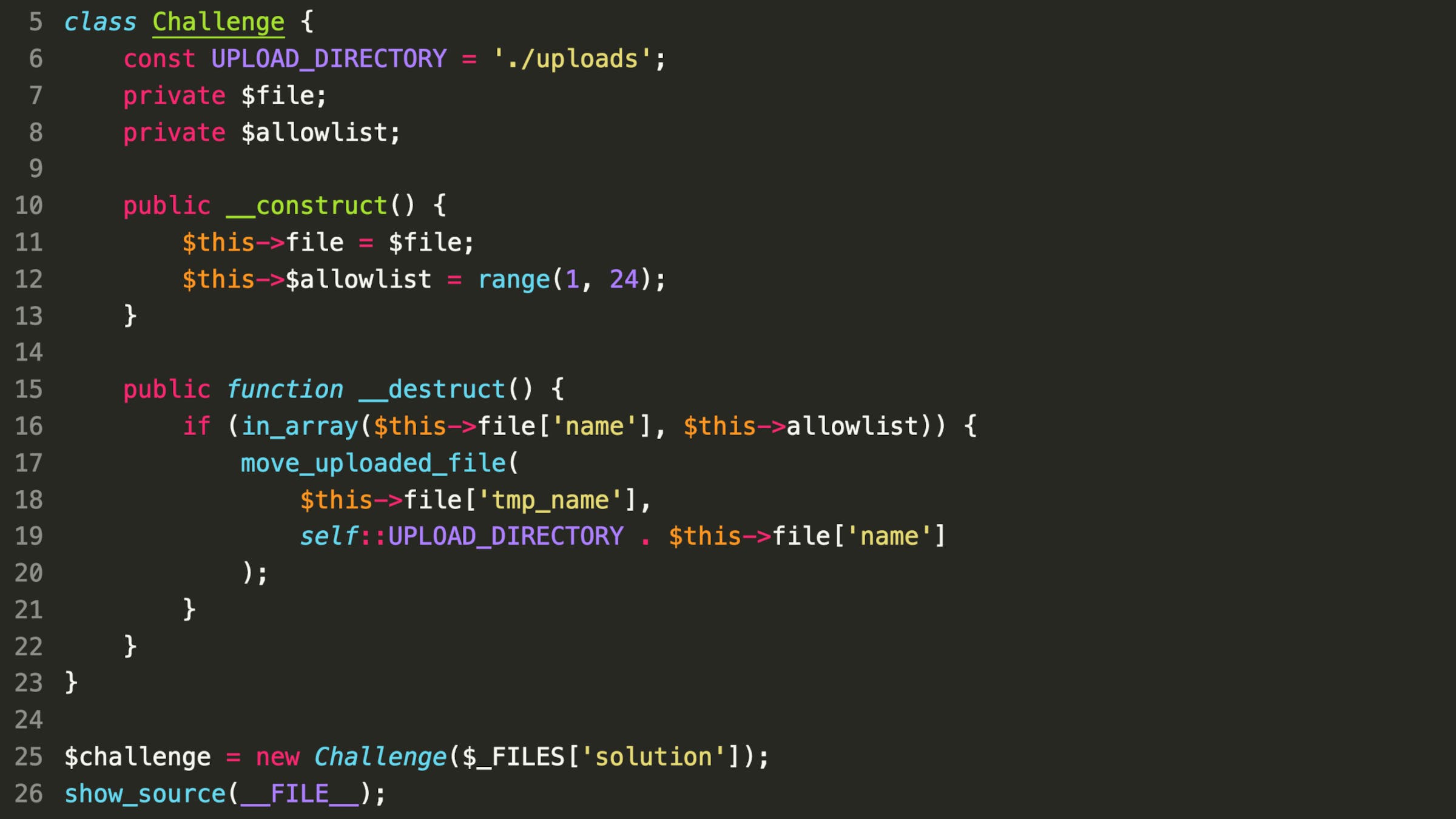
Real-world code vulnerabilities
At SonarSource, we spend a lot of time studying and understanding real-world vulnerabilities in order to continuously push our code analysis to the next level. We crafted 24 realistic security bugs and tricks based on what we saw in real, production code during this year's security research. Some of these challenges may look harder than usual at first, but don’t worry: play around with the code snippet, experiment, and enjoy the “aha moment” when you discover the answer!
We want to make this event enjoyable for all skill sets and levels, so we'll release hints throughout the day (if needed) and a detailed solution after 24 hours. To learn as much as you can from these challenges and get a grasp on all the “tricks” involved, do not just identify the impact of the vulnerability (say, Remote Code Execution), but try to think of how it could be exploited, what would be the steps to follow, etc.
Even more languages!
Our code analysis technology is constantly improved to detect vulnerabilities in the most popular programming languages. Last year, we crafted challenges for 4 server-side languages, namely Java, C#, PHP and Python. This year, we decided to also cover C / C++ and JavaScript.
And even if the day’s security challenge isn’t in your favorite language it’s worth looking at because the principles carry across languages and will sharpen your security skills for 2022.
With 24 Vulnerabilities and Security Hotspots
Our products support over 4,000 rules because there are many different kinds of mistakes you can make on the way to writing clean code. In this year’s Code Security Advent Calendar, we focus on 24 different types of vulnerabilities that can have a major impact on your application and user security.
Every challenge will hide at least one security flaw. Sometimes it's based on unvalidated or unsanitized user input, sometimes on a bad configuration, and sometimes it's a harmless-looking feature that can be abused by attackers.
Gifts
Our elves will look carefully at all your answers. The most active players with the best solutions will be contacted on Twitter after the end of our Code Security Advent Calendar to receive a cool swag pack. Let’s get started!
We wish you all a happy and healthy December season!
If you don’t use Twitter you can also join the discussion in our community forum.

