Sonar's latest blog posts
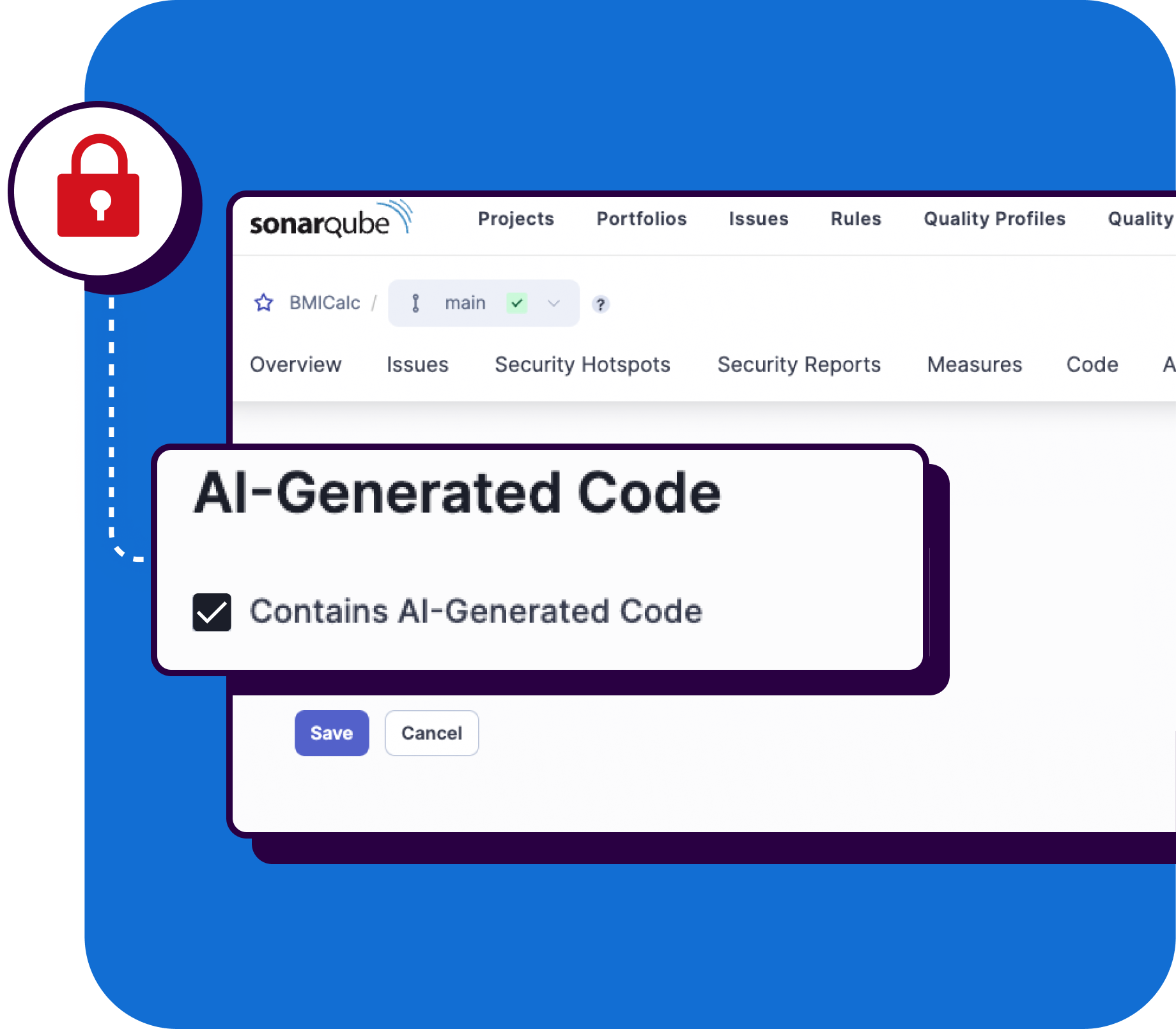
Building Confidence and Trust in AI-Generated Code
To tackle the accountability and ownership challenge accompanying AI-generated code, we are introducing Sonar AI Code Assurance

Lesser spotted React mistakes: What are we even rendering?
This series is dedicated to the small, but common pitfalls and errors you can encounter when writing React code. Whether an experienced JavaScript | TypeScript developer or just starting out, the results can be surprising.
Read Blog post >
Cacti: Unauthenticated Remote Code Execution
Learn how we discovered a critical vulnerability in Cacti with the help of SonarQube Cloud.
Read Blog post >
Get new blogs delivered directly to your inbox!
Stay up-to-date with the latest Sonar content. Subscribe now to receive the latest blog articles.

SonarQube Server 9.8 is here!
The latest version of SonarQube Server from Sonar has arrived. Check out what’s new in SonarQube Server 9.8 in this quick video and download it now.
Read Blog post >

Develop Your Cloud Native Apps the Sustainable Way
Application development using cloud native technologies is a game changer for developers. With a robust, maintainable codebase, they are positioned to do their best work. Learn how Sonar has the clean code game plan to perfectly complement your cloud native initiatives.
Read Blog post >

Sonar @ Pwn2Own Toronto 2022
Members of the Sonar Vulnerability Research team remotely participated in Pwn2Own Toronto 2022. This competition is quite special for us: we usually focus on code vulnerabilities in open-source web application projects.
Read Blog post >

How to enable your development team to deliver Clean Code?
Regardless of the company we work for, the project we contribute to, or our years of experience as individual developers or as a team, we inevitably make mistakes while coding. On average, a development team generates about 15 to 50 errors per 1,000 lines of delivered code.
Read Blog post >

Scaling Clean Code Across the Enterprise
Code is at the core of your software and dictates its behavior and performance. Clean code makes it easier for your development teams to introduce changes and enhancements to software because it is free of issues.
Read Blog post >
What I learned from using SonarQube Server for the first time
In this blog, I will share the story of how I got introduced to SonarQube Server and made use of it as a team lead. I will explain how it helped us improve our code, and also assisted me in growing a team of junior developers with a Clean Code companion by their side.
Read Blog post >

Code Security Advent Calendar 2022
The year is slowly coming to an end and it’s time again to look back and reflect on the great fun and achievements of the year. This is where we would like to thank our community and share a little gift, as we do every December since 2016.
Read Blog post >

Lesser spotted React mistakes: Zombie methods
This series is dedicated to the small, but common pitfalls and errors you can encounter when writing React code. Whether an experienced JavaScript | TypeScript developer or just starting out, the results can be surprising. Part 2.
Read Blog post >
Doing More with Less in Uncertain Times
Even though efficiency of all work processes is a goal of any business striving for success, it is even more of a challenge given the current economic climate. This bar shifts higher every day.
Read Blog post >
