Members of our Vulnerability Research team remotely participated in Pwn2Own Toronto 2022. This competition is quite special for us: we usually focus on code vulnerabilities in open-source web application projects. It's a perfect opportunity for our team to look at a broader scope, study different vulnerability types, and challenge ourselves.
What's Pwn2Own?
This event is organized by the Zero Day Initiative (ZDI), part of Trend Micro.
The goal of this competition is to find and exploit vulnerabilities on devices part of a list announced a few months before, most of the time best-selling electronics like routers, phones, printers, etc. Contestants have to demonstrate exploits for vulnerabilities on fully up-to-date targets in their default configuration by executing arbitrary commands and sometimes starting a light show by taking control of the device's LEDs.
It is important to note that vulnerabilities are acquired by ZDI, and later disclosed to the affected vendors; ZDI wants to encourage coordinated disclosure practices and does not redistribute the information they acquired that way. This point is crucial for us, and our disclosure policy is very similar to the one they enforce.
This year is the biggest edition of Pwn2Own so far, with 66 entries by 26 teams; most entries target best-selling IoT devices (i.e., routers, NAS), with only a few notable exceptions like the Samsung Galaxy S22 and the Sonos One Speaker.
Routers are a special category, as competitors can demonstrate attacks via two distinct vectors: LAN-side, from the local network, or WAN-side, directly connected to the upstream ethernet port. It can lead to very impressive vulnerabilities, where the attacker only needs the public IP address of the router to compromise over the Internet!
If you want to learn more about this event through words from previous winners, we recommend Amat Cama's interview on Hack'nSpeak (in French) and Charlie Miller's on Security Conversations.
Our entries…
We chose to work on four devices and discovered a total of 4 valid entries:
- 1 x WAN-side on the Synology RT6600ax
- 1 x WAN-side on the NETGEAR RAX30
- 2 x LAN-side on the NETGEAR RAX30
However, days only before the end of the registration period, NETGEAR released a new version of their firmware. This update patched many vulnerabilities; in our case, we couldn't exploit our LAN-side and WAN-side vulnerabilities. That doesn't mean they were all fixed, sometimes they applied only temporary workarounds, and we'll work with the vendor to ensure they are aware of all our findings.
As it appears that these routers do not automatically apply updates, we strongly recommend updating your device if you have one at home. We highly recommend STAR Labs' analysis if you want to read more about the vulnerabilities patched in the latest firmware update.
These last-minute patches are now fairly common during Pwn2Own. We are, however, afraid that such practices are not suitable for customers as vendors withhold security releases until the very last minute.
Meanwhile, we registered our Synology entry for the competition. On December 5th, organizers live-streamed the random drawing to determine the order of attempts. This is a crucial step, as an entry will be deemed valid only if no other contestant has leveraged the same vulnerability before. And… we were picked last of the whole event, with two other contestants presenting findings on the same device before us.
…Our entry
We demonstrated our vulnerability on December 9 at 20:30 and we successfully took control of the Synology RT6600ax on the WAN interface!
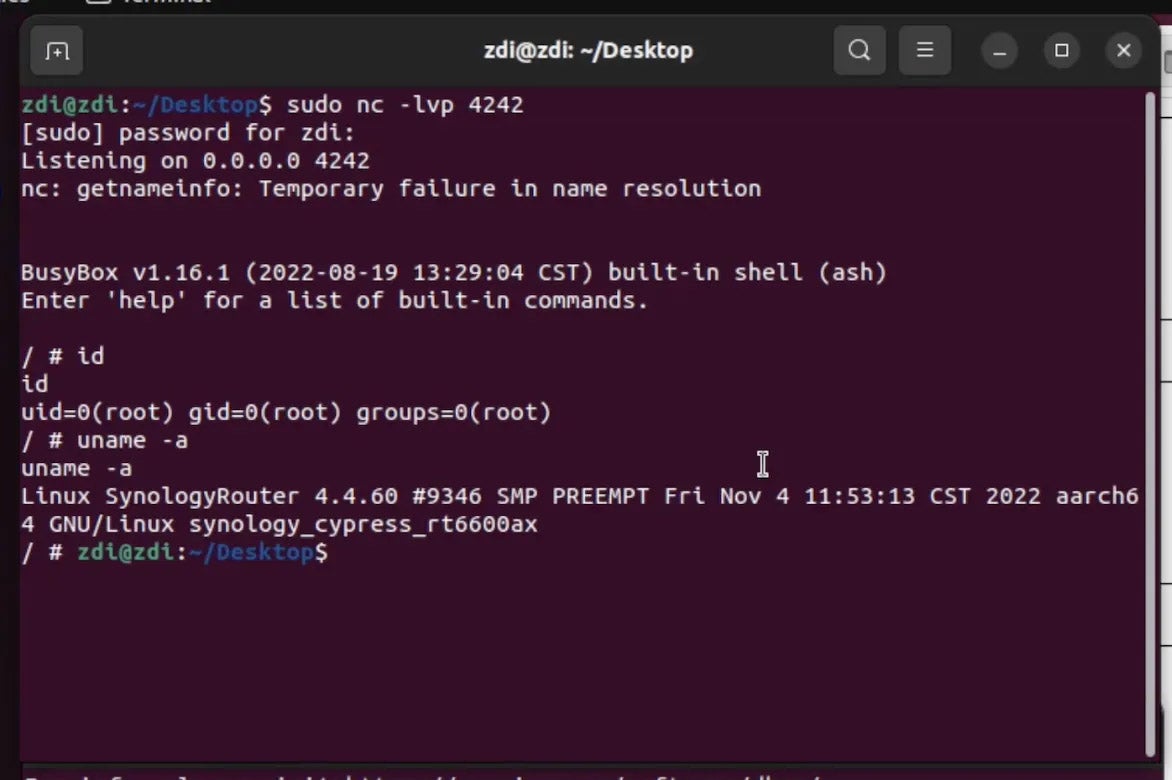
Unfortunately for us, other contestants already used the same vulnerability earlier in the contest. We already guessed it as ZDI made the following announcement on December 7 and the bug class involved in our submission was similar:
What we demonstrated is still a valid entry, and we are proud to have been able to make it happen despite all the hurdles on the way.
Closing words
We would like to thank all Zero Day Initiative organizers for their flexibility and help in making our remote attempt run smoothly. Other teams demonstrated very impressive findings, and the Taiwanese team DEVCORE was crowned Master of Pwn for their successful entries. On our side, we had fun doing our research and hope to participate again next year! The vulnerability is now in Synology's hands and should be patched within the next 90 days.
Looking back at the early patches and our research, we can't help but notice the security of end-user routers (and, in general, IoT devices) still lacks most security best practices. Such events help raise awareness of the importance of secure development as soon as possible in the software development lifecycle.

