I think we'd all agree that 2020 has been quite a year. Here at SonarSource, one bright spot in this tumultuous year was SonarSource’s acquisition of RIPS Technologies. After joining forces in May we've spent the last six months merging not just our two SAST technologies to build a super-powerful new engine, but also merging two companies and cultures.
Since 2016, an annual tradition at RIPS was the hosting of a Security Advent Calendar. Each calendar released 24 little gifts in the form of code challenges that offered fun and security training (2016, 2017, 2018, 2019). This was always a nice way to give something back to the community at year-end. And this is something that we would like to continue at SonarSource this year.
So let's have some fun together!
How you can participate
Starting on December 1st, we will release a daily code challenge on Twitter. Can you spot the vulnerability? You can follow us on Twitter to easily subscribe to our challenges, share it with your friends, and discuss solutions and feedback in the comments. We will join the discussion too and also share our intended solutions.
Challenge accepted? Follow @SonarSource on Twitter.
What you can expect
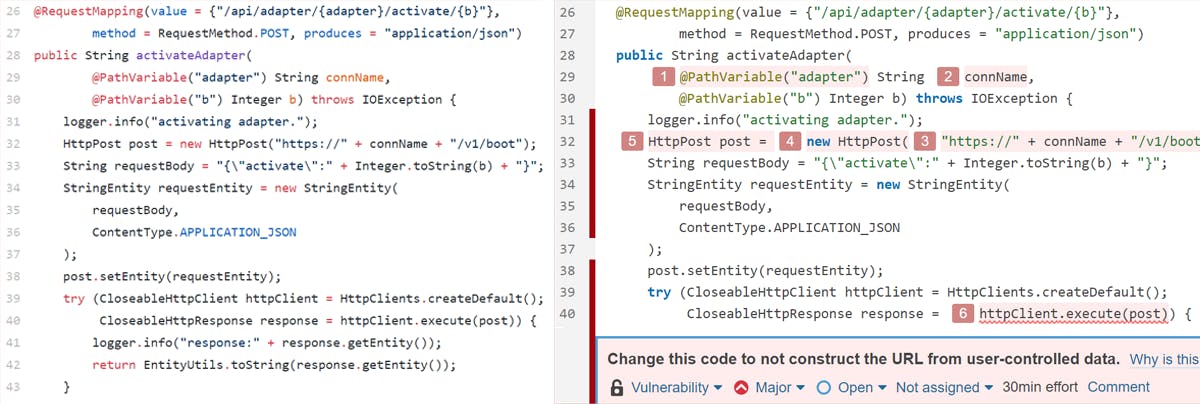
Code from real-world applications
Every day, SonarQube Cloud analyzes millions of lines of code for issues and helps open source developers fix them. We investigated some of the security findings in public repositories and selected interesting coding mistakes. In some cases, we had to modify the vulnerable code lines a bit to make them fit into an interesting challenge, but each vulnerability is based on an original in a real-world application.
With 24 Vulnerabilities and Security Hotspots
Our products support over 4,000 rules because there are many different kinds of mistakes you can make on the way to writing clean and secure code. In our Code Security Advent Calendar, we focus on 24 different types of Vulnerabilities and Security Hotspots that can have a major impact on your application and user security. Every challenge will hide at least one security flaw. Sometimes it's based on unvalidated or unsanitized user input, sometimes on a bad configuration, and sometimes it's a harmless-looking feature that can be abused by attackers. But don’t worry, the challenges are designed for developers, not security experts, and our solutions are there to help.
In 4 of the most popular languages
Our new SAST technology is constantly improved to detect vulnerabilities in the most popular programming languages. For our code challenges that focus on application security, we selected the following popular server-side languages this year: Java, C#, PHP and Python. And even if the day’s security challenge isn’t in your favorite language it’s worth looking at because the principles carry across languages and will sharpen your security skills for 2021.
We wish you all a happy and healthy December season!
If you don’t use Twitter you can also join the discussion in our community forum.

