Sonar's latest blog posts
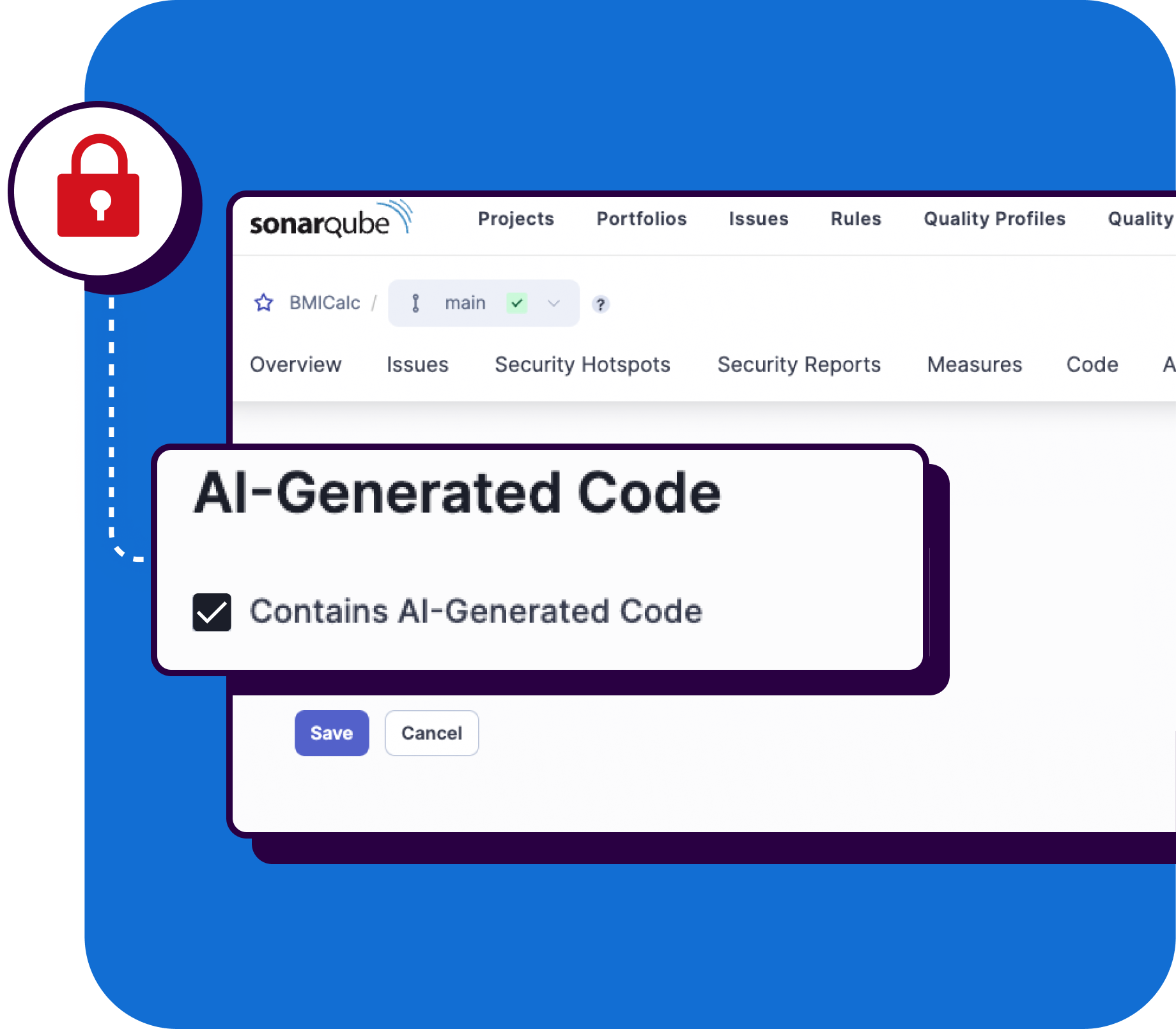
Building Confidence and Trust in AI-Generated Code
To tackle the accountability and ownership challenge accompanying AI-generated code, we are introducing Sonar AI Code Assurance
Grav CMS 1.7.10 - Code Execution Vulnerabilities
We responsibly disclosed two code execution vulnerabilities in Grav CMS, one of the most popular flat-file PHP CMS in the market. Let’s see what we can learn from them and discuss their patches!
Read Blog post >

NoSQL Injections in Rocket.Chat 3.12.1: How A Small Leak Grounds A Rocket
We recently discovered vulnerabilities in Rocket.Chat, a popular team communications solution, that could be used to take over Rock.Chat instances.
Read Blog post >
Get new blogs delivered directly to your inbox!
Stay up-to-date with the latest Sonar content. Subscribe now to receive the latest blog articles.

What to expect from JavaScript/TypeScript analysis on OWASP JuiceShop
In April 2021, we updated our JavaScript and TypeScript SAST engines to explore more execution flows, increase performance and improve overall accuracy. It now goes far beyond what we did in the past for these languages. With this post, we’re going to tell you what you can expect for these languages, and more specifically which vulnerabilities can be detected.
Read Blog post >
SonarQube Server 8.9 LTS: 3 steps to a smooth upgrade
SonarQube Server 8.9 Long Term Support (LTS) is officially here! Check out this list of tips & tricks on how to upgrade your environment from start to finish.
Read Blog post >
PHP Supply Chain Attack on Composer
We recently discovered a vulnerability in Composer, the main package manager for PHP, and were able to use it to take over the central repository, packagist.org.
Read Blog post >
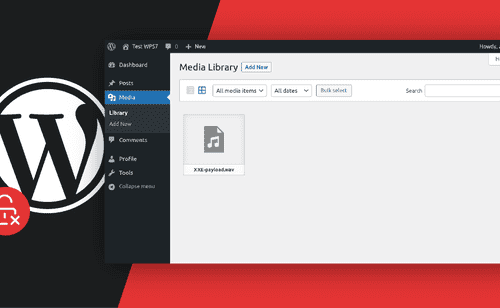
WordPress 5.7 XXE Vulnerability
In this blog post we analyze a XXE vulnerability that our analyzers discovered in WordPress, the most popular CMS, and what PHP 8 developers can learn from it.
Read Blog post >

Code Vulnerabilities in NSA Application Revealed
Our security research team discovered multiple code vulnerabilities in the NSA's Java application Emissary. Find out more about these issues and related attacks.
Read Blog post >

Mono-repository support for Bitbucket Cloud now available for SonarQube Cloud!
Last September, we announced that mono-repository support was added for GitHub and Azure DevOps Services. The good news is: mono-repository support is now also available for Bitbucket Cloud! See what it brings and how you can configure it in SonarQube Cloud.
Read Blog post >

My Support Engineer Journey at SonarSource
What does a Support Engineer do and how could it ever be interesting? Here we share more about a unique and rewarding journey in this role at SonarSource that will help you understand more about the job and opportunity.
Read Blog post >
MyBB Remote Code Execution Chain
Today SonarSource is pleased to share a guest contribution to our Code Security blog series about learnings from a chain of serious vulnerabilities in MyBB.
Read Blog post >
Hack the Stack with LocalStack: Code Vulnerabilities Explained
Our vulnerability researchers found critical code vulnerabilities in a popular Python application that can be exploited remotely, even when the application instance is hosted locally.
Read Blog post >
