Sonar's latest blog posts
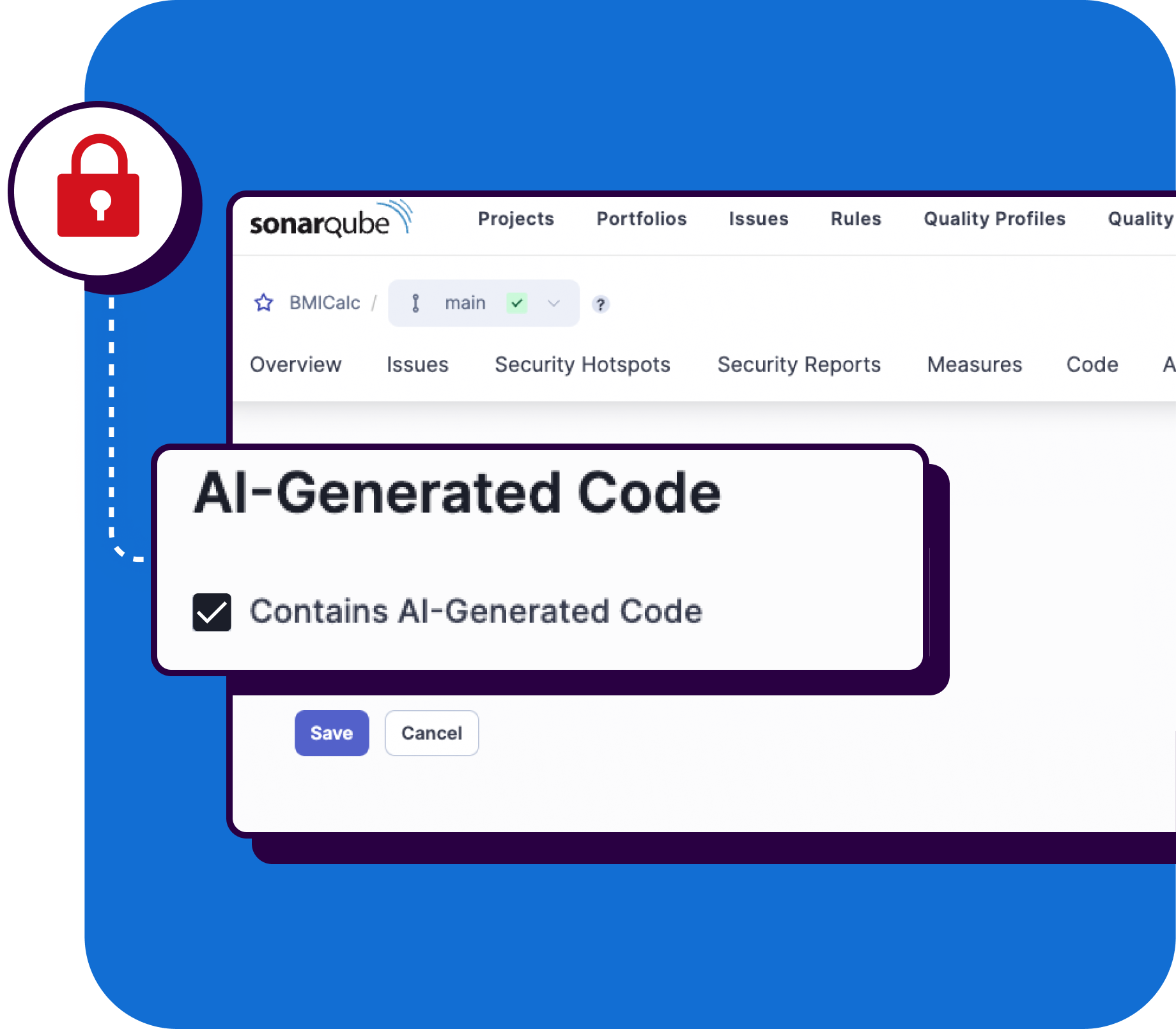
Building Confidence and Trust in AI-Generated Code
To tackle the accountability and ownership challenge accompanying AI-generated code, we are introducing Sonar AI Code Assurance

The npm package of the Moment: How we migrated from a deprecated Javascript package
Moment.js is a popular date-handling library that, at one point, was being downloaded nearly 15 million times a week. Despite its popularity, Moment’s open source maintainers announced in September 2020 that they were deprecating the project.
Read article >
Checkmk: Remote Code Execution by Chaining Multiple Bugs (3/3)
This last article of the series determines how an attacker can chain two further vulnerabilities to fully take over a Checkmk server.
Read Blog post >
Get new blogs delivered directly to your inbox!
Stay up-to-date with the latest Sonar content. Subscribe now to receive the latest blog articles.

A Look Back at KubeCon 2022
The Sonar Team had a great time sponsoring KubeCon 2022 in Detroit. Read about our takeaways from the event...
Read Blog post >

Checkmk: Remote Code Execution by Chaining Multiple Bugs (2/3)
The second article of this series outlines how an attacker can leverage the ability to forge arbitrary LQL queries to gain access to the NagVis component.
Read Blog post >

Evaluating the RAIL license family
Machine learning (ML) is the hot topic in tech circles right now, and tech lawyers are no exception. Virtually every lawyer discussion I’ve had in the last two weeks has ended with a variation on this question
Read article >

Checkmk: Remote Code Execution by Chaining Multiple Bugs (1/3)
We discovered multiple vulnerabilities in Checkmk, which can be chained together by an unauthenticated, remote attacker to fully take over a vulnerable server.
Read Blog post >

Beyond the Rules of Three, Five and Zero
After examining the Rules of Three, Five, and Zero, part 2 of this series looks at the exceptions that prove the rule(s). Some of them may surprise you (no, really)!
Read Blog post >

Bits from Hexacon 2022
Our AppSec and Vulnerability Research teams had a great time at Hexacon 2022, here's what we enjoyed!
Read Blog post >

Lesser spotted React mistakes: Hooked on a feeling
This series is dedicated to the small, but common pitfalls and errors you can encounter when writing React code. Whether an experienced JavaScript | TypeScript developer or just starting out, the results can be surprising.
Read Blog post >

SonarQube Server 9.7 is here!
Check out what’s new in SonarQube Server 9.7 in this quick video.
Read Blog post >
Remote Code Execution in Melis Platform
We come back on a critical deserialization vulnerability identified by our SAST engine in the software Melis Platform. Let’s look at how it works under the hood and how we confirmed its exploitability.
Read Blog post >
